Packet switching is the fundamental protocol that lets the Internet and Local Area Networks function in their decentralized, user-directed, constantly evolving ways. The idea is to group data to be transmitted into discrete blocks known as packets. Because information is confined to discrete regions that have defined beginnings and endings, they can coexist without mixing or mutual interference. This greatly boosts the efficiency, accuracy and reliability of the transmissions through diverse media.
There are various protocols, but the basic idea is that packets, composed of headers and payloads, are transferred and reassembled. As for the Internet, websites are conveyed in the form of HTML text files, with graphics sent separately and placed correctly thanks to browsers.
Packet switching was employed at the inception of the Internet and was originally conceived as a means by which the network, used for military connections, could survive attack. In our post-cold war environment with terrorism threats, this attack hardening is as relevant as ever. Packets originate and flow through multiple channels and the process is totally decentralized. The destruction of one or even many locations can never paralyze our network connectivity. Another advantage of packet switching is that limited network resources are used to better advantage because there’s no requirement for continuous open connections.
There are two types of packet switching, connectionless (datagram switching) and connection-oriented (virtual circuit switching). The difference is in how address information is conveyed.
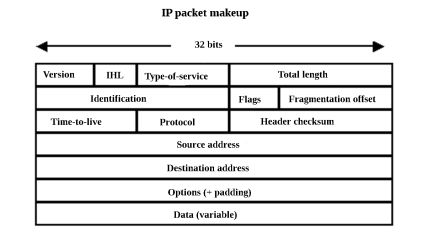
In connectionless packet switching, Ethernet and Internet Protocol (IP) are the two dominant technologies. Each packet, in its header, contains complete addressing information. For this reason, it is possible for the various packets to be conveyed via different routes, some quite circuitous. A consequence is that the packets are likely to arrive out of order. Pertinent information is contained in the header so the reassembled data makes sense at the receiving end.
The other packet-switching mode, connection-oriented transmission, incorporates a connection identifier rather than an address in each header. This removes some bulk from the transmitted data packets (in the headers) but it necessitates a preliminary setup phase before packet transmission can begin.
Each packet has two parts, control information and content intended for the recipient, commonly referred to as the payload. Control information, not necessarily seen by the human recipient, contains instructions for the network to deliver user data. Included are network addresses for the source and destination. There are also error detection codes and sequencing information. This type of data is contained in the packet headers and trailers, which as the names imply, precede and follow the payload.
It is possible for a complete packet containing header and trailer to be carried as the payload in another packet, inserted between higher-level headers and trailers.
Communication cannot take place between two or more electronic devices unless they agree on a protocol. Internet Protocol and Transmission Control Protocol (TCP) are examples. These two together comprise a significant part of the Internet Protocol Suite, and they are commonly referred to as TCP/IP.
The World Wide Web (www), email, File Transfer Protocol (FTP), secure shell, peer-to-peer file sharing and streaming media applications all make use of TCP. It emphasizes reliability over speed. That is why users experience a degree of latency. But it is a small price to pay for the knowledge that in the huge Internet environment a great deal of connectivity and file transfer takes place all the time with relatively little signal corruption, data loss or dropout. That is due to TCP’s great ability to seek out and correct errors. What makes this work is packet transmission.
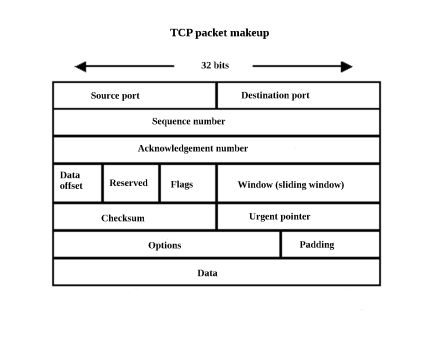
The 32-bit acknowledgment number field can contain the value of the next sequence number that the sender of the segment is expecting to receive. The sequence number refers to the stream flowing in the same direction as the segment, while the acknowledgment number refers to the stream flowing in the opposite direction from the segment.
Important parts of the TCP protocol are establishment and termination of the connection. TCP uses a three-way handshake to establish the connection. For a client to connect to a server, first the server listens at a port prior to establishing a passive open. Then, the client creates an active open. The connection termination involves a four-way handshake. Here again each side participates in accordance with the protocol.
To function properly, TCP utilizes ordered data transfer, retransmission of lost packets, error-free data transfer, flow control and congestion control. These constituent elements, agreed upon in advance, are integral parts of TCP and facilitate our reliable Internet.

Tq
My doubt are cleared